Table of Contents
Introduction
Understanding the foundational aspects of Bitcoin is crucial for all users, whether they are new or experienced. This guide is designed to help you recover bitcoin wallet, Bitcoin keys and addresses, giving you a clear path to regain access to your bitcoin in different situations. If you wish to understand better the foundational aspects of your wallet, keep reading, else you can skip to the section that talks about recovering lost bitcoin.
Recover Bitcoin Wallet: Understanding Bitcoin’s Cryptographic Foundations
Bitcoin’s revolutionary approach to decentralized finance hinges on its use of cryptography, specifically public-key cryptography, to ensure the secure ownership and transfer of funds. Here’s how it works:
1. Private Key Creation
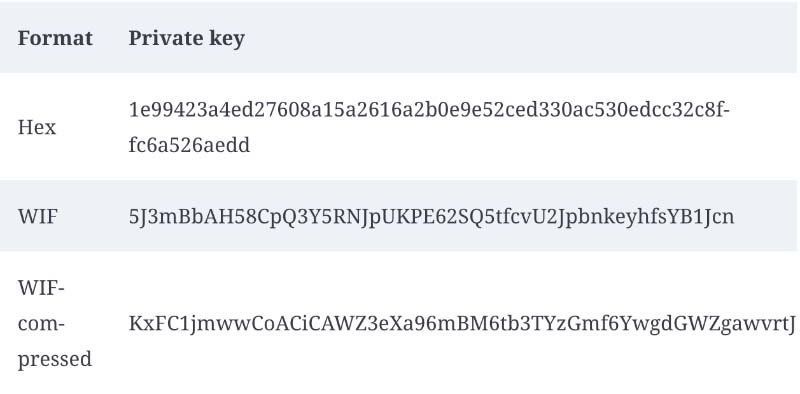
Every Bitcoin wallet begins with the creation of a private key. This key is a 256-bit number chosen randomly within the range defined by the Secp256k1 elliptic curve standards. Virtually no number falls outside this range, ensuring every private key is unique and secure.
What is a Cryptographic Key?
Think of a cryptographic key as a special kind of secret code or password that can lock (encrypt) or unlock (decrypt) information. Just like a physical key can lock or unlock a door, a cryptographic key can secure data so that only someone with the right ‘key’ can read it.
What is an Elliptic Curve?
An elliptic curve in cryptography is like a set of mathematical rules that creates a playground for securing information. It’s a curved line that has special properties. When we use these properties in calculations, we can create strong ‘locks’ for our digital information that are very hard to break without the ‘key’.
2. Public Key Derivation
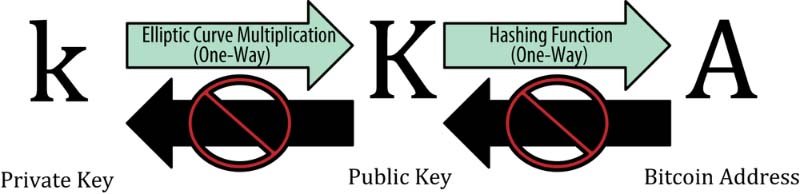
From this private key, a public key is derived through Elliptic Curve Cryptography (ECC). This process is a one-way function—meaning that while anyone can generate a public key from a private key, the reverse is impossible. This is the essence of asymmetric cryptography: it allows you to share your public key without compromising the security of your private key.
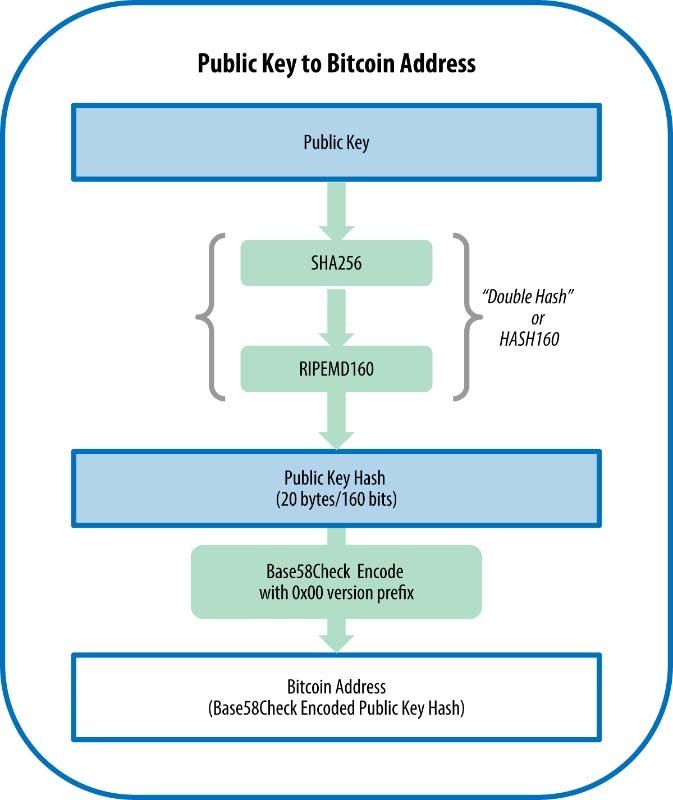
3. Bitcoin Address Generation
The public key is not typically what you share with others; instead, it’s hashed using SHA256 and RIPEMD160 functions to create a public key hash. This hash is then encoded into a Bitcoin address using Base58, a format that is compact and easy to read. This address is what you provide to others to receive Bitcoin.
What is SHA256?
Imagine SHA256 as a super complex blender for data. You throw in any amount of ingredients (your data), and it blends them into a smoothie (a fixed-size output) that looks nothing like the original ingredients. No matter how many times you blend the same ingredients, you’ll always get the same smoothie, but you can’t ever get the original ingredients back from the smoothie. This unique blend represents your data securely and consistently every time. The U.S. government requires its agencies to protect certain sensitive information using it.
What is a Public Key Hash?
A public key hash is like a unique nickname for your public key in the world of cryptography. Just like you might use a nickname that’s easier for friends to remember than your full name, a hash is a shorter and more convenient version of your public key. It helps keep your real public key private while still allowing you to receive Bitcoin transactions securely.
What is RIPEMD160?
RIPEMD160 is a way of shortening information, similar to condensing a long story into a brief summary. It takes input, like a public key, and outputs a shorter, fixed-length sequence of numbers and letters. This summary is unique; even the smallest change in the original story creates a completely different summary, making it a useful tool for verifying the integrity of data.
What is Base58?
Base58 is like an alphabet for computers to communicate numbers and letters in a way that is easier for humans to read and write. It’s a method of writing data that avoids characters that might look similar, like ‘0’ (zero) and ‘O’ (the letter O), reducing the chance of errors when copying or transcribing. This is especially helpful in the world of Bitcoin, where making a mistake in a long address could mean sending money to the wrong place.
4. Digital Signatures:
When you wish to send bitcoin, you must prove ownership without revealing your private key. This is done through a digital signature produced by the Elliptic Curve Digital Signature Algorithm (ECDSA). This signature is proof that the transaction was authorized by the owner of the private key, without ever exposing it.
Types of Wallets and Key Management
The Bitcoin ecosystem has evolved to offer various wallet types, each with its own approach to key management. They consist of Non-deterministic (Random) Wallets, Deterministic (Seeded) Wallets, and Hierarchical Deterministic Wallets (HD Wallets, BIP-32/BIP-44). The key structures among them vary significantly. Here’s a breakdown of the keys used in each of these wallet types:
Non-deterministic (Random) Wallets
These are the simplest forms, where each private key is generated independently and randomly. There’s no connection between the keys, necessitating individual backups for each.
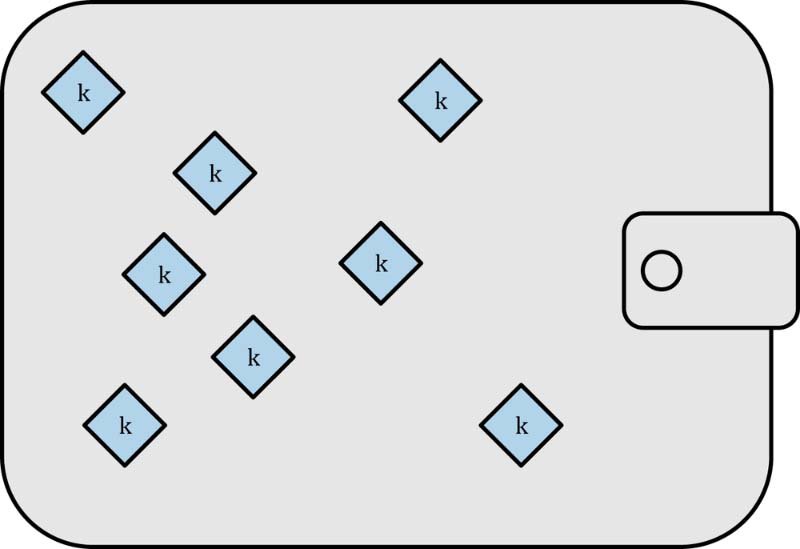
- Individual Private Keys: Each key is generated randomly and independently. There is no mathematical relationship between these keys.
- Individual Public Keys: Each public key is derived from its corresponding private key.
- Individual Bitcoin Addresses: Each address is generated from its corresponding public key.
In Nondeterministic wallets, each key and address is a standalone entity, requiring each private key to be backed up separately.
Deterministic (Seeded) Wallets
As a significant advancement, these wallets use a single seed to generate all subsequent keys. If you have the seed, you can recreate all the keys and addresses associated with your wallet.
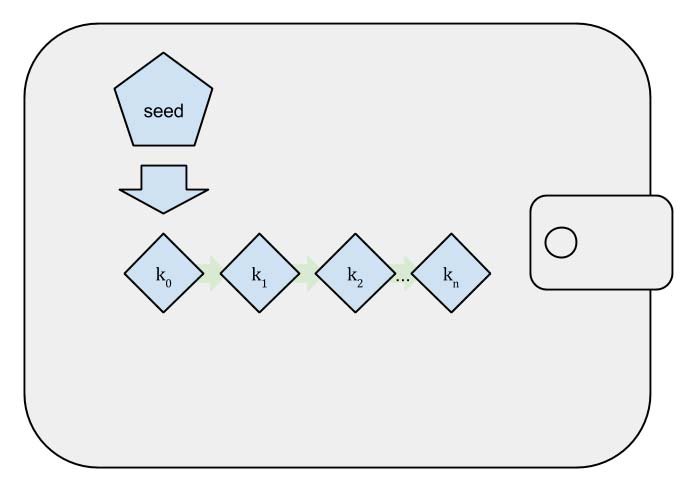
- Seed (Root Private Key): A single seed (root private key) is used to generate all other keys. This is usually represented as a mnemonic phrase for ease of use.
- Derived Private Key: Generated from the seed using a deterministic algorithm.
- Derived Public Keys: Each is derived from its corresponding private key.
- Bitcoin Addresses: Each address is created from its respective public key.
In Deterministic Wallets, backing up the seed (root private key or mnemonic phrase) is enough to recover all associated addresses and funds.
Hierarchical Deterministic Wallets (HD Wallets, BIP-32/BIP-44)
These wallets take key generation a step further. From the master seed, a master private key is created, along with a master public key and a master chain code. This master public key can then be used to generate a tree of child keys, each of which can produce further grandchild keys, allowing for a structured and organized system of addresses and keys that can all be restored from the initial seed.
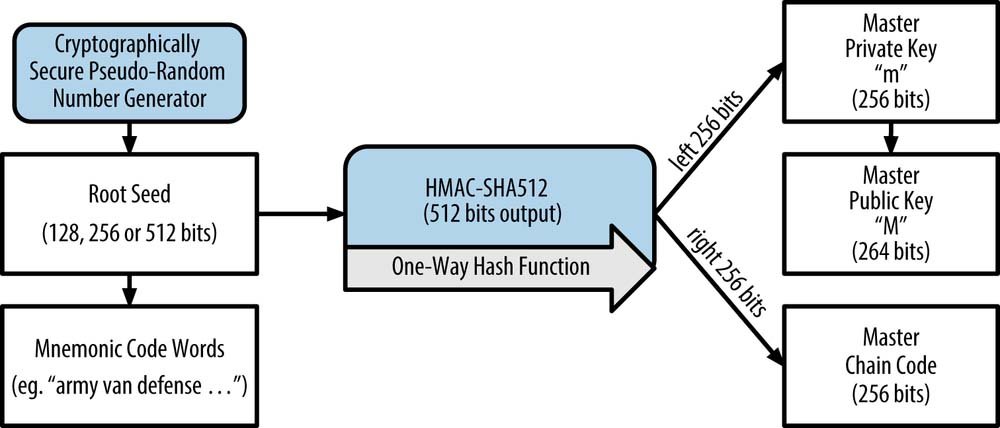
- Root Seed: The starting point for all key generation, which can also be converted into a Mnemonic Phrase, often represented by 12-24 English words.
- Master Private Key: Generated from the root seed through a one-way hash function.
- Master Public Key: Derived from the master private key, used to generate public keys/addresses without exposing the private keys.
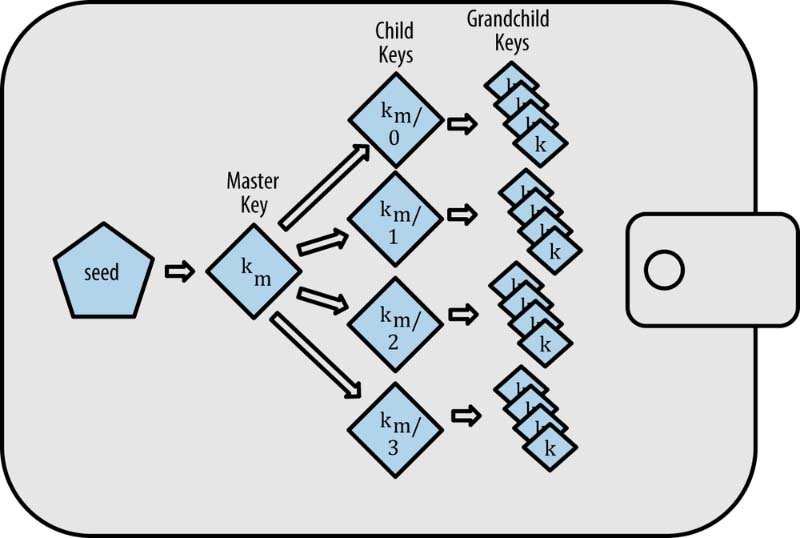
- Hierarchical Private Keys: Generated from the master private key, following a tree structure (hierarchy).
- Hierarchical Public Keys: Each is derived from its corresponding hierarchical private key.
- Bitcoin Addresses: Generated from the hierarchical public keys.
HD Wallets, particularly those conforming to BIP-32/BIP-44 standards, offer a structured way to generate multiple keys and addresses from a single seed. This makes backup and recovery more streamlined, as only the root seed (or mnemonic phrase) needs to be secured.
BIP-39
BIP39 has been the go-to method for generating recovery codes for years, translating a sequence of bytes into a series of words. A user’s wallet presents a sequence of words that encode the wallet’s backup, allowing for recovery and re-creation of all derived keys.
The use of a passphrase adds a layer of security, essentially creating an infinite array of potential wallets from a single recovery code. This optional passphrase enables a second security factor and can also serve as a form of plausible deniability.
Conclusion
Each of these wallet types represents an evolution in key management, offering different levels of convenience, security, and backup efficiency. Understanding the cryptographic underpinnings of Bitcoin is essential for anyone involved in the space.
It not only helps secure funds but also empowers users to make informed choices about their wallet types and management strategies. If you want to learn more about the evolution of Bitcoin wallets over the years, give this article a read. Now, let’s delve into the recovery process in case of lost or misplaced backups.
A Guide Through Common and Uncommon Scenarios
Losing access to Bitcoin keys can induce panic, but understanding the nature of your wallet and the available recovery options can turn the tide. Here’s a deeper dive into what you can do in different scenarios using Electrum wallet:
“I lost my wallet! What can I do?”
1. Retrace Your Steps
Sometimes, the issue is not a complete loss but a misplacement. Search through your files, secure storages, and other potential hiding spots. It’s not uncommon to find your backup stored in a safe place and have simply forgotten its location.
2. Import Your Private Key
If you’ve lost access to your wallet application or hardware device but still have your private key stored elsewhere, many wallet applications allow you to import this key directly. This will give you immediate control over your funds.
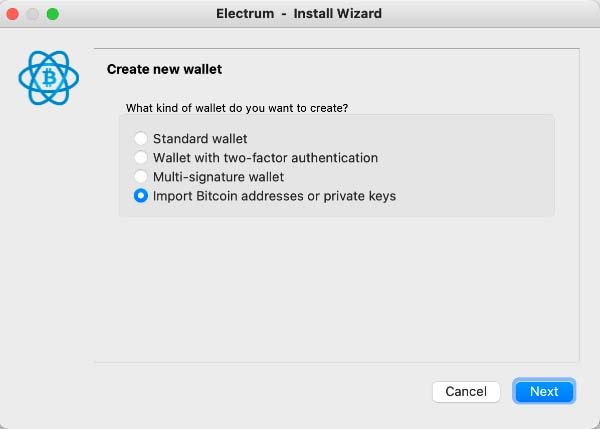
Next > Import Bitcoin addresses or private keys > Enter WIF keys
3. Import Your Mnemonic Backup
If you have a mnemonic phrase or a seed backup, you can recover your entire wallet (including all derived keys) by importing it into a compatible wallet application. This is one of the most common and reliable methods for wallet recovery.
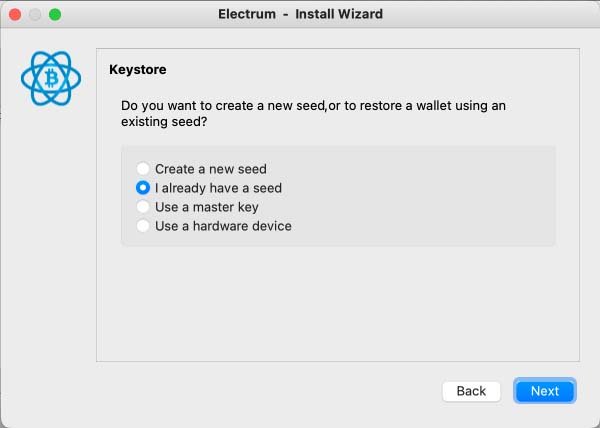
Next > Standard wallet > I already have a seed > Enter your seed phrase
4. Sweep the Wallet
Sweeping a wallet refers to creating a new transaction to transfer all funds from an old wallet into a new one. This can be done by entering your private keys or mnemonic phrase into a new wallet application, which will then initiate the transfer.
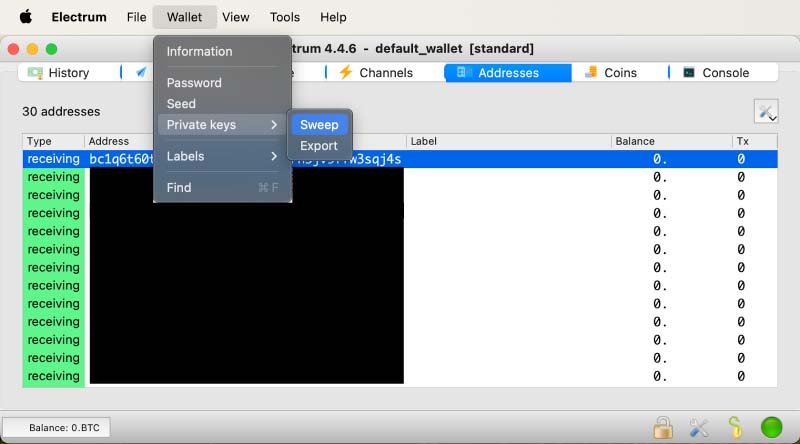
Open your newly created wallet > Wallet > Private keys > Sweep > Enter WIF key
Wallets like Electrum, Bitcoin Core, and Blockstream Green provide a ‘sweep’ feature for your funds. Unlike importing, which retains the same private key, sweeping imports the funds and then transfers them to a new wallet with a different private key. This is done as a best security and privacy practice.
“My bitcoin is on an exchange, how do I get it off?”
If your bitcoin is on an exchange and you want to transfer it to a personal wallet for more control or security, you’ll need to:
- Set up a personal wallet, ensuring it’s secure and backed up.
- Obtain a receive address from your personal wallet.
- Initiate a withdrawal from the exchange to that address.
Make sure to transfer a small amount first to ensure everything works smoothly before transferring the rest.
Related reading: Custodying Your Bitcoin: Combating Institutional Control Over Your Finances
Edge Cases
I have a Multi-signature Scheme
- You have all of the private keys used to create the scheme: You’re in full control. Use a wallet that supports multisig to spend or transfer funds.
- You have enough keys to meet the quorum and the Wallet’s Master Public Key: You can still access your funds. In a multisig wallet, the master public key and quorum keys can be used to reconstruct the necessary signatures to execute transactions.
- If you lack the minimum amount of keys or meet the quorum but do not have the wallet’s master public key to reconstruct the redemption script, then your bitcoin is likely lost.
I Used a Passphrase
If you’ve used a passphrase with your mnemonic phrase, you’ll need to remember it to access your funds. Without it, even the mnemonic phrase won’t be sufficient, as each passphrase leads to a different set of derived keys (effectively, it’s a new wallet).
I Only Have SeedXOR Backup Left
SeedXOR is a method of splitting your seed into parts. You’ll need all the parts to reconstruct the original seed. Once you have the pieces, combine them using the XOR operation to recover your original seed.
I Am Missing Words from Mnemonic Backup
Tools like FinderOuter or btcrecover can assist in recovering a mnemonic phrase when only a few words are missing. They use the known words and the structure of the mnemonic to guess the missing parts. Using these tools does require some technical skills and a proper setup to avoid compromising your private key. Also, if you attempt brute-forcing, know that it gets exponentially more difficult the more words you need to uncover.
My Bitcoin Was Stolen (Observed Outgoing Transaction)
Unfortunately, if the transaction is confirmed on the blockchain, it’s irreversible. Your focus should shift to security—understanding how the theft occurred and enhancing your wallet’s protection to prevent future occurrences. Report the theft to the relevant authorities, and if the amount is significant, consider getting legal help.
Future-Proof Your Wallet

Creating additional backups of your recovery phrase is crucial. Store these in multiple secure locations or on engraved steel plates. Post-recovery, enhance your Bitcoin security:
- Store recovery phrases in secure, diverse locations.
- Regularly inspect private key backup locations to ensure their integrity.
- Use multi-signature wallets or a passphrase for extra security.
- Keep wallet software up-to-date.
- Keep a copy of your wallet fingerprint.
- Note down the derivation path, especially if not using a default path.
- Engrave or stamp your private key in steel to timeproof your backup.
Conclusion
No matter the scenario, the best defense against losing access to your Bitcoin is a good offense: meticulous backups, a clear understanding of your wallet’s recovery processes, and regular checks to ensure your recovery information is accurate and accessible. With the right preparations, recovering your Bitcoin, even in complex situations like multisig schemes or lost passphrases, is a manageable task.
All images used in the “Understanding Bitcoin’s Cryptographic Foundations” section are from https://github.com/bitcoinbook/bitcoinbook
Antonopoulos, Andreas M. “Mastering Bitcoin 2nd Edition – Programming the Open Blockchain.” GitHub, 2018, https://github.com/bitcoinbook/bitcoinbook. Accessed 25 November 2023.
Screenshots of Electrum wallet have been taken by the author of this article.
FAQ
u003cstrongu003eWhat is the foundational aspect of Bitcoin’s security?u003c/strongu003e
Bitcoin relies on cryptography, specifically public-key cryptography, to ensure the secure ownership and transfer of funds.
u003cstrongu003eHow is a private key created in Bitcoin?u003c/strongu003e
A private key is a 256-bit number chosen randomly within the range defined by the Secp256k1 elliptic curve standards.
u003cstrongu003eWhat is a cryptographic key in the context of Bitcoin?u003c/strongu003e
A cryptographic key is a special code or password used to lock or unlock information. It secures data so that only someone with the right key can access it.
u003cstrongu003eWhat is the role of an elliptic curve in Bitcoin’s cryptography?u003c/strongu003e
An elliptic curve creates a secure playground for securing information in cryptography. It’s a set of mathematical rules that allows the creation of strong digital locks.
u003cstrongu003eHow is a public key derived from a private key in Bitcoin?u003c/strongu003e
Elliptic Curve Cryptography (ECC) is used to derive a public key from a private key. It’s a one-way function, ensuring the security of the private key.
u003cstrongu003eHow is a Bitcoin address generated from a public key?u003c/strongu003e
The public key is hashed using SHA256 and RIPEMD160 functions, then encoded into a Bitcoin address using Base58.
u003cstrongu003eWhat is the purpose of SHA256 in Bitcoin?u003c/strongu003e
SHA256 is a cryptographic hash function that secures data by blending it into a fixed-size output, making it secure and consistent.
u003cstrongu003eWhat is a public key hash in Bitcoin?u003c/strongu003e
A public key hash is like a unique nickname for a public key in cryptography, making transactions secure while keeping the actual public key private.
u003cstrongu003eHow does Base58 contribute to Bitcoin address encoding?u003c/strongu003e
Base58 is a method of writing data that avoids characters that might look similar, making it easier for humans to read and write Bitcoin addresses.
u003cstrongu003eWhat is the role of digital signatures in Bitcoin transactions?u003c/strongu003e
Digital signatures, produced by the Elliptic Curve Digital Signature Algorithm (ECDSA), prove ownership of a private key without revealing it during a transaction.
u003cstrongu003eWhat are the different types of Bitcoin wallets?u003c/strongu003e
There are Non-deterministic (Random) Wallets, Deterministic (Seeded) Wallets, and Hierarchical Deterministic Wallets (HD Wallets, BIP-32/BIP-44).
u003cstrongu003eHow does a Deterministic Wallet differ from a Non-deterministic Wallet?u003c/strongu003e
Deterministic Wallets use a single seed to generate all subsequent keys, allowing for easier backup and recovery, while non-deterministic wallets produce private keys randomly.
u003cstrongu003eWhat is the significance of Hierarchical Deterministic Wallets (HD Wallets)?u003c/strongu003e
HD Wallets offer a structured way to generate multiple keys and addresses from a single seed, streamlining backup and recovery.
u003cstrongu003e14. What is BIP-39, and how is it used for wallet recovery?u003c/strongu003e
BIP-39 translates a sequence of bytes into a series of words, creating a mnemonic phrase for wallet backup and recovery.
u003cstrongu003eHow can a passphrase enhance wallet security in Bitcoin?u003c/strongu003e
A passphrase adds an extra layer of security, creating an infinite array of potential wallets from a single recovery code.
u003cstrongu003eWhat should I do if I lose access to my Bitcoin keys?u003c/strongu003e
Retrace your steps and find either your mnemonic phrase or your private keys. Then import your private key or mnemonic backup, or use the u0022sweepu0022 feature in wallet applications like Electrum.
u003cstrongu003eHow can I transfer Bitcoin from an exchange to a personal wallet?u003c/strongu003e
Set up a secure personal wallet, obtain a receive address, and initiate a withdrawal from the exchange to that address.
u003cstrongu003eWhat should I do if my Bitcoin is stolen with an observed outgoing transaction?u003c/strongu003e
If the transaction is confirmed on the blockchain, it’s irreversible. Focus on enhancing wallet security, report the theft, and consider legal assistance for significant amounts.
u003cstrongu003eHow can I recover a mnemonic phrase with missing words?u003c/strongu003e
Tools like FinderOuter or btcrecover can assist in recovering a mnemonic phrase when only a few words are missing, but technical skills are required.
u003cstrongu003eWhat are the best practices for securing Bitcoin and preventing loss of access?u003c/strongu003e
Regularly inspect private key backup locations, use multi-signature wallets or a passphrase for extra security, keep wallet software up-to-date, and store recovery phrases in secure, diverse locations.